When your company uses a cloud-based phone system, you might assume your calls are safe-hidden away behind firewalls and encryption. But what if someone else using the same cloud platform could listen in? Or access your call logs, voicemails, or user data? This isn’t science fiction. It’s the real risk of poor shared tenant isolation in Cloud VoIP systems.
What Exactly Is Tenant Isolation in Cloud VoIP?
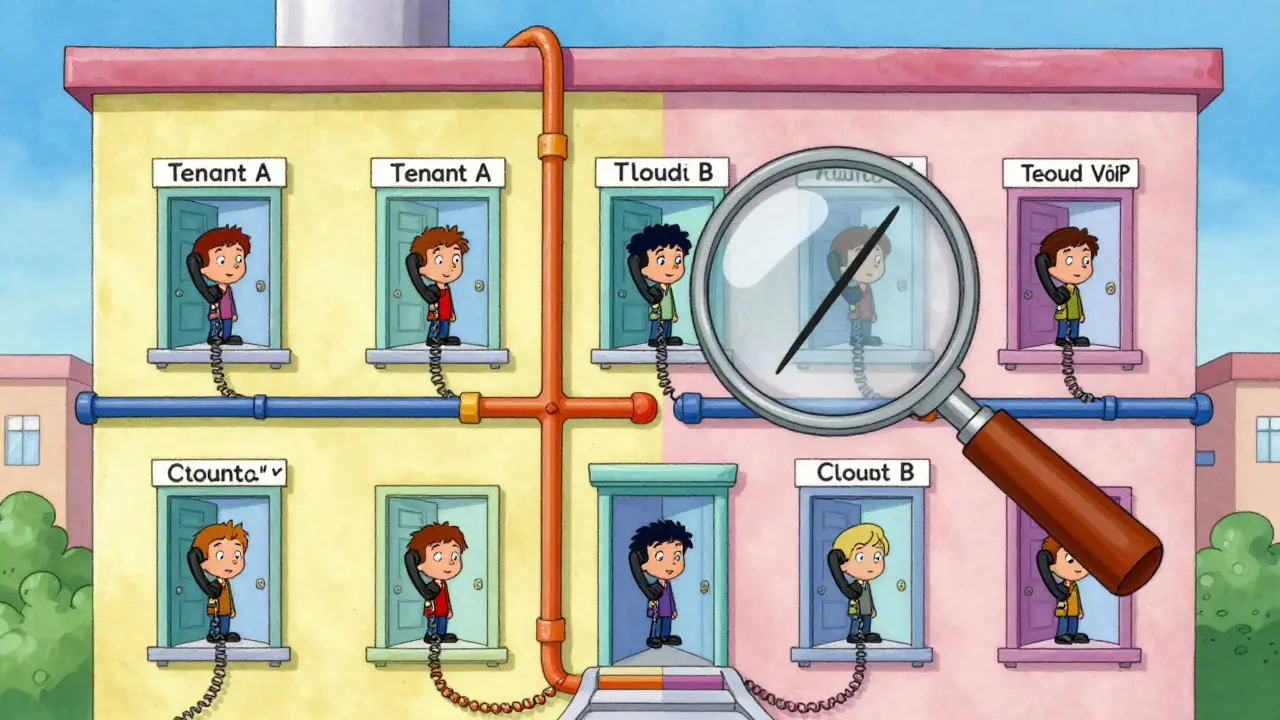
Think of a Cloud VoIP platform like a shared apartment building. Each tenant (your company, a client, a partner) has their own apartment-private phone lines, locked doors, personal mailboxes. But they all share the same building’s wiring, elevators, and utilities. Tenant isolation is the system that makes sure your apartment stays yours. No one else can sneak in, tap your line, or peek at your records-even if they’re on the same network. In technical terms, multi-tenant isolation means separating voice data, user accounts, call metadata, and admin controls so that one customer’s information can’t leak into another’s. This isn’t optional. Voice data is among the most sensitive types of enterprise information. It includes names, phone numbers, payment details, medical conversations, legal discussions, and internal strategies. If that data crosses tenant boundaries, you’re not just at risk-you’re in violation of GDPR, HIPAA, PCI DSS, and other regulations.How Do Cloud VoIP Providers Actually Isolate Tenants?
There’s no single way to do this. The best providers layer multiple controls to create defense-in-depth. Here’s what actually works:- Network Segmentation: Each tenant gets a virtual network-often using VLANs or VPCs-that keeps their traffic physically separate from others. Even if two companies are on the same server, their data flows through isolated pipes.
- Encryption Per Tenant: Every call uses AES-256 encryption, but here’s the key: each tenant has their own unique encryption key. No shared keys. No backdoors. Even the provider can’t decrypt your calls without your key.
- Containerization with Namespaces: Platforms like Twilio and Vonage run each tenant’s services in isolated Docker or Kubernetes containers. This prevents one tenant’s software from interfering with another’s-even if a bug or hack occurs.
- Role-Based Access Control (RBAC): Four-tier permissions are standard: system admin, tenant admin, user admin, end user. A support rep at your company can’t access another tenant’s call history. Even your own IT team can’t see data outside their assigned tenant.
- API Gateways with Tenant-Specific Tokens: Every API call to the VoIP system must include a token tied to a specific tenant. RingCentral’s system, for example, blocks 83% more unauthorized API attempts than platforms with shared API endpoints, according to ESG Lab testing.
- Log Isolation: Audit trails must be tenant-specific. If you’re audited for GDPR, you need to prove your call logs were never mixed with another company’s. 41% of platforms failed this in 2023, according to the Cloud Security Alliance.
Multi-Tenant vs. Single-Tenant: What’s the Real Trade-Off?
You might think: “If isolation is so hard, why not go single-tenant?” It sounds safer. And for some, it is. But it’s also much more expensive and slower to scale.| Feature | Multi-Tenant | Single-Tenant |
|---|---|---|
| Cost per User | $15-$25/month | $25-$40/month |
| Deployment Time | 2-4 weeks | 8-12 weeks |
| Scalability | Automatic, handles 10,000+ concurrent calls | Manual provisioning, slower scaling |
| Security Incidents (2021-2023) | 22% linked to poor isolation | Under 5% (infrastructure is dedicated) |
| Regulatory Preference (Healthcare) | 73% use with strict controls | 27% prefer due to physical separation |

Where Tenant Isolation Falls Short (And How to Spot It)
Even top providers aren’t perfect. Here are the common weak spots:- Shared API Endpoints: If your VoIP provider lets all tenants use the same API gateway, a compromised token from one tenant can open doors to others. Ask: “Do you use tenant-specific API keys?” If they say “We use OAuth,” push further. OAuth alone isn’t enough without tenant context.
- Weak Logging: If you can’t export clean, tenant-only audit logs, you can’t prove compliance. Look for platforms that let you filter logs by tenant ID in real time.
- No Behavioral Monitoring: Most systems only block known threats. The next wave of attacks will exploit subtle side-channel leaks-like CPU cache timing (think Meltdown/Spectre). Providers like Microsoft now offer hardware-enforced isolation zones for financial and government clients. If you’re in a high-risk industry, ask if your provider has this.
- Zero Trust Gaps: Gartner found 68% of Cloud VoIP platforms lack contextual access controls. Just because someone is logged in doesn’t mean they should access that data. Are user sessions checked for device posture? Location? Time of day? If not, you’re relying on outdated perimeter security.
What You Should Demand from Your VoIP Provider
Don’t take marketing claims at face value. Here’s what to ask before signing a contract:- Can you show me your SOC 2 Type II report? Specifically, does it validate tenant isolation under Control ID CC-DATA-06?
- Do you use per-tenant encryption keys? Can I rotate them myself?
- Is every API call authenticated with a tenant-bound token? Can you demonstrate this with a test?
- Can I export audit logs that exclude all other tenants’ data?
- Do you use containerized isolation (Docker/Kubernetes namespaces)?
- Have you been audited for side-channel vulnerabilities like CPU cache leaks?





Fred Edwords
16 Dec 2025 at 06:27Just read this through twice-because it’s that important. Tenant isolation isn’t some optional nicety; it’s the firewall between your CEO’s private negotiation and a random startup’s IT intern. AES-256 per-tenant keys? Check. Containerized namespaces? Check. API tokens bound to tenant IDs? Non-negotiable. If your provider uses shared endpoints, run. Not walk. Run. And don’t let them distract you with SOC 2 buzzwords-ask for the exact control ID: CC-DATA-06. If they don’t know it, they’re winging it. And in voice security? Wingin’ it is how you end up on the front page of TechCrunch… as a cautionary tale.